Applied Sciences | Free Full-Text | An Overview of Cyber Threats, Attacks and Countermeasures on the Primary Domains of Smart Cities

What Is Network Behavior Anomaly Detection? Definition, Importance, and Best Practices for 2022 - Spiceworks

Protein-Based Virtual Screening Tools Applied for RNA–Ligand Docking Identify New Binders of the preQ1-Riboswitch | Journal of Chemical Information and Modeling

Mission‐centric decision support in cybersecurity via Bayesian Privilege Attack Graph - Javorník - 2022 - Engineering Reports - Wiley Online Library
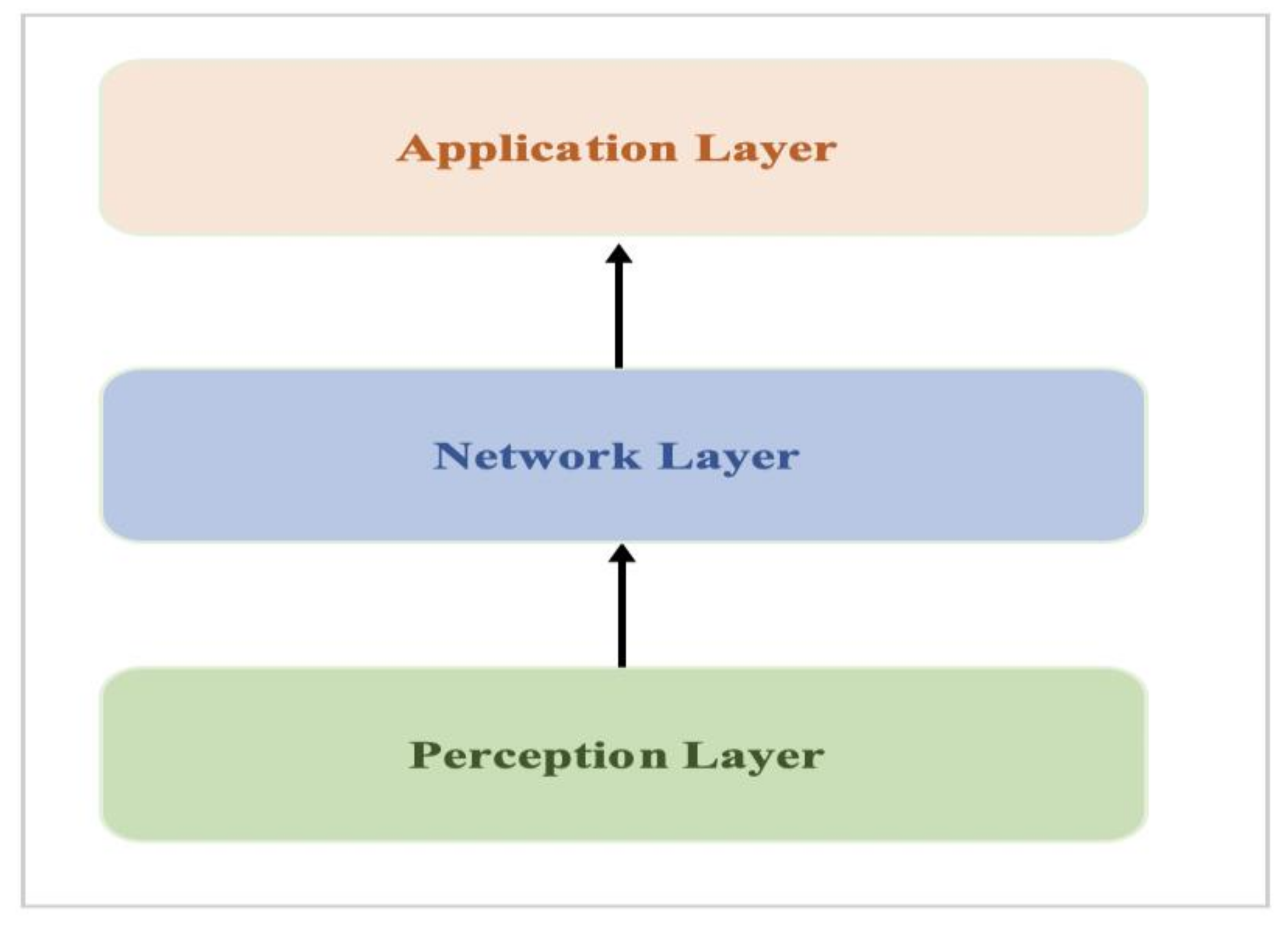
Electronics | Free Full-Text | Cybersecurity Threats, Countermeasures and Mitigation Techniques on the IoT: Future Research Directions




![20 Top Cyber Security Tools in 2023 [Most Powerful Tools] 20 Top Cyber Security Tools in 2023 [Most Powerful Tools]](https://intellipaat.com/blog/wp-content/uploads/2021/06/Top-20-Cyber-Security-Tools-Big.png)